A digital signature certifies and timestamps a document. If the document is subsequently modified in any way, a verification of the signature will fail. A digital signature can serve the same purpose as a hand-written signature with. Dmg vs pgp signature. Dmg vs pgp signature. Oct 09, 2016 What's the difference? Save hide report. This thread is archived. New comments cannot be posted and votes cannot be cast. Best top new controversial old q&a. Level 1 deleted 8 points 2 years ago. The first is the program itself, the second is a PGP signature. PGP stand for Pretty Good.
One of the requirements forpublishing your artifacts to the Central Repository, is that they have beensigned with PGP. GnuPG or GPG is a freely availableimplementation of the OpenPGP standard. GPG provides you with the capability togenerate a signature, manage keys, and verify signatures. This page documentsusage of GPG as it relates to the Central Repository. In a nutshell you will have to
- create your own key pair
- and distribute it to a key server so that users can validate it
Installing GnuPG⚓︎
Download GPG from http://www.gnupg.org/download/or install it with your favorite package manager and verifyit by running a gpg command with the version flag.
Note that on some systems the newer gpg2 will be used:
Generating a Key Pair⚓︎
A key pair allows you to sign artifacts with GPG and users can subsequentlyvalidate that artifacts have been signed by you. You can generate a key with

Select the default value when asked for the kind (RSA) and the size (2048bit) of the key. The time ofvalidity for the key defaults to never expire. However it is commonly suggested to use a value ofless than 2 years. Once they key is expired you can extend it, provided you own the key andtherefore know the passphrase.
As a next step you have to provide your name, email, and a comment for thekey. These identifiers are essential as they will be seen by anyone downloadinga software artifact and validating a signature. Finally, you can provide apassphrase to protect your secret key. It is essential that you choose a securepassphrase and that you do not divulge it to any one. This passphrase and yourprivate key are all that is needed to sign artifacts with your signature.
Listing Keys⚓︎
Once key pair is generated, we can list them along with any otherkeys installed:
The output displays the path to the public keyring file. The line starting withpub shows the length (1204D), the keyid (C6EED57A), and the creation date(2010-01-13) of the public key.
The next line shows the UID of the key, which is composed of a name, a comment,and an email. The last line shows sub-keys, we don’t need to worried about thisfor now.
To list the private keys you can use
The output is similar to the one provided for the public keys.
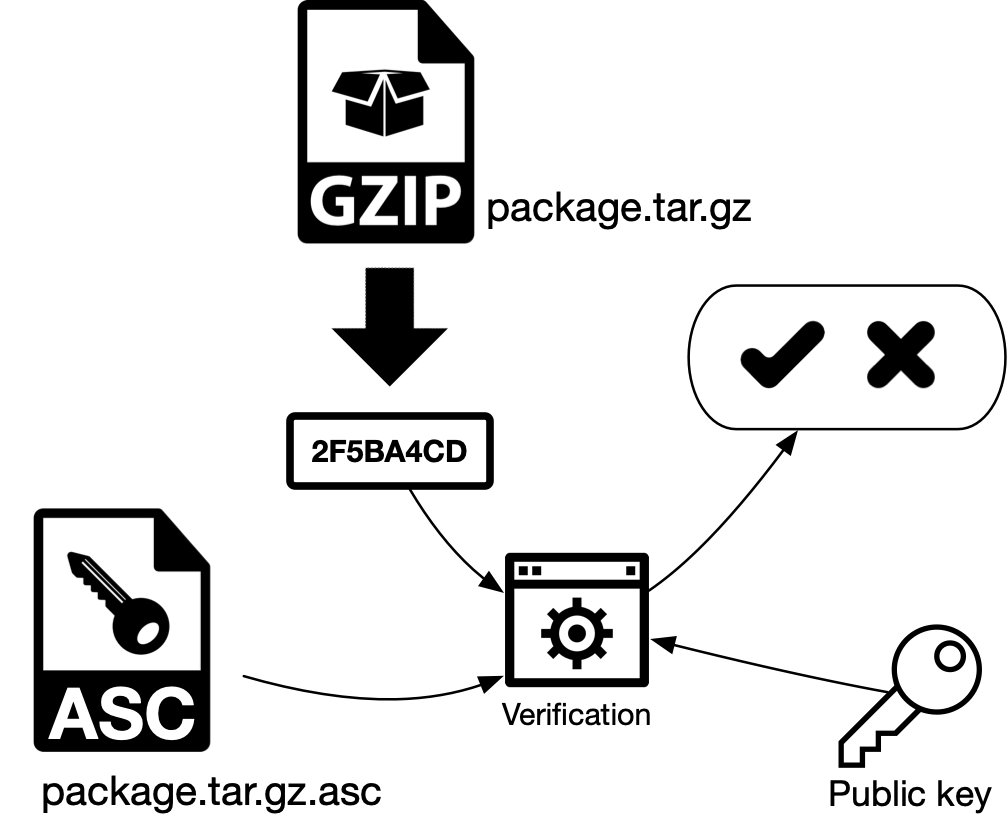
Signing a File⚓︎
To create an ASCII formatted signature for any file, run the following gpgcommand:
The -a option tells gpg to create ASCII armored output, the -b option tellsgpg to make a detached signature. If your private key has a passphrase, you willbe asked for it. Without a passphrase, all someone needs to forge an artifactsignature is your private key. The passphrase is an extra level of protection.
GPG will create a file like temp.java.asc , which is the signature of temp.java. You will want to distribute it along with the main file so the other canverify the main file using your public key:
Distributing Your Public Key⚓︎
Since other people need your public key to verify your files, you have todistribute your public key to a key server:
The --keyserver parameter identifies the target key server address and use --send-keysis the keyid of the key you want to distribute. You can get your keyid bylisting the public keys. Once submitted to a key server, your public key will besynchronized to other key servers.
Now other people can import your public key from the key server to their local machines:
Using Build Tools for Signing⚓︎
Now that you have created and distributed your key, you can proceed to get the componentsautomatically signed as part of your build. Depending on your build tool this setup willbe different and you can find out more about these next steps in the specific sections:
Dealing with Expired Keys⚓︎
When you generate your PGP key, you need to specify how long the key should bevalid. After that period you can edit your existing key to extend it's validtime.
For example, I have a key pair which expires on 2012-02-27:
You can edit a key with the following command using the key id as parameter:
There is only one key to edit, so I choose 1:
You will see the * after (1), which mean you've selected this key to edit.To edit the keys expiration time, enter the following command:
Enter what you need, for example 10m (10 months), and confirm it.The last step about editing is saving it what you've done:

Now you can see your key's expires time is updated:
Finally, distribute your public key again:
Dmg Vs Pgp Signature File
Delete a Sub Key⚓︎
Some PGP tools generates sub keys and use them for signing by default, but tomake Maven tools recognize the signature, you must use the primary key to signyour artifacts.
Some PGP tools by default generate a sub signing key and use it for signinginstead of using the primary key. This is a problem if you use it to signartifacts and deploy artifacts to the Central Repository, because Maven as wellas Nexus Repository Manager can only verify against a primary key.
To fix this problem you have to delete the sub signing key so PGP will use theprimary key for signing. To get an idea whether you have a sub signing key,run command below with your own key ID:
As you can see from above example, this key has 2 sub keys with ID DD289F64and 8738EC86 . The output also shows the creation time and expiration time.What's important here is the usage of these keys. E stands for Encryption sosub key DD289F64 is used for encryption only, S stands for Signing so sub key8738EC86 is used for Signing only.
If a primary key has a S sub key, it will use it for signing, otherwise itselfwill do signing job. So, in our example, we want to delete the sub key 8738EC86 .
First select the sub key we want to delete, since its index is 2 (indicesstarts with 0), we run command:
As you can see from the output, the sub key 8738EC86 is marked with *. Now delete it:
Tip
Dmg Vs Pgp Signature Program
If you've already distributed your public key, it's better to revoke the subsigning key instead of deleting it, although either way you can make yourprimary key as the signing key. To revoke a sub key, use the revkey command instead ofdelkey.
Dmg Or Pgp Signature
Now that 8738EC86 is not listed any more, the final step is saving our change:
Dmg Vs Pgp Signature
That's it! Now you can test the change by signing a file, and then verify it.The output should contain something like: